Privileged access management is a critical identity governance component of a cybersecurity risk reduction strategy. Threat actors often target over-privileged accounts to gain unauthorized access, exfiltrate sensitive data, introduce malicious activity, or engage in other forms of malicious behavior. By employing effective privilege management tools, organizations can significantly reduce their attack surface and mitigate the potential damage from security breaches or insider threats. Policies that support the principle of least privilege and restrict access to privileged resources can help to limit the risk of security incidents and preserve the confidentiality, integrity, and availability of critical data and assets.
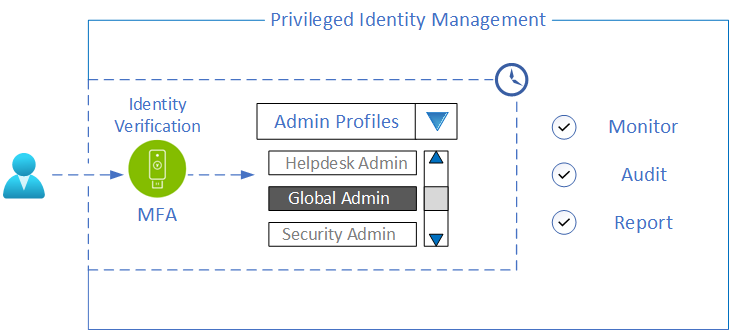
Azure Active Directory (AAD) Privileged Identity Management (PIM) facilitates the management of privileged access to Azure AD and Azure resources by enforcing a Zero Standing Privilege (ZSP) security model. This model only grants users elevated access privileges when necessary and for a limited time, instead of providing persistent access. With PIM, organizations can grant Just-in-Time (JIT) access to privileged roles, assign temporary or time-bound roles, and require multi-factor authentication for role elevation. These controls help organizations reduce the attack surface and prevent unauthorized access to sensitive data and resources, thereby improving their overall security posture.
To further enhance security, organizations can enforce the use of hardware security keys, such as YubiKeys, for privilege elevation activation with PIM, driven by Conditional Access using Authentication Strengths and Authentication Context. Authentication Strengths can now allow organizations to granularly enforce strong, phishing-resistant multi-factor authentication (MFA) based on applicable threat models, such as requiring YubiKeys using FIDO2 or Certificate-Based Authentication (CBA). This approach provides greater control in strengthening an organization’s security posture.
Step-up authentication is a security measure that requires users to provide additional verification when accessing important resources or performing sensitive tasks. This can include things like multifactor authentication, where users must provide additional information beyond their usual login credentials. With Conditional Access Authentication Context, organizations can enforce strong security measures for sensitive tasks, such as requiring the use of a hardware authenticator like the YubiKey. By using context-based policy enforcement, organizations can ensure that sensitive operations are always verified using the strongest possible authentication methods.
Identity is now the control plane, and enabling MFA is the single most crucial step organizations can take to secure their users. Privileged identities require stricter controls, as they are more vulnerable to identity-related attacks that can compromise information, disrupt operations, and cause reputational damage. Therefore, it is crucial to implement solutions that can securely manage and monitor privileged access across the digital estate.
With Azure PIM, Conditional Access Authentication Context and Authentication Strengths, organizations can secure privilege elevation by providing JIT access and enforce MFA to activate any privileged role using YubiKeys.
For additional information on Privileged Access Management and what it means for your business, check out our page here. For a step-by-step setup of how to get the Azure PIM solution enabled with your YubiKey, watch our video below.





