What is Phishing-Resistant MFA?
Account takeover (often abbreviated ATO) describes the scenario where a cybercriminal or organization uses stolen or compromised credentials to gain fraudulent access to an account, and then exploits the privileges granted or associated to said account. All manner of account types may be viable targets, including but not limited to email, banking, online shopping and even corporate or employee accounts. A classic example of an ATO would be a hacker that gains access to someone’s online bank account, and then initiates a wire transfer to steal the funds therein.
Phishing-Resistant MFA Definition
Phishing-resistant MFA is multi-factor authentication (MFA) that is immune from attempts to compromise or subvert the authentication process, commonly achieved through phishing attacks, which includes but is not limited to spear phishing, brute force attacks, man-in-the-middle attacks, replay attacks and credential stuffing. Phishing resistance within an authentication mechanism is achieved by not only requiring that each party provide proof of their identity but also intent through deliberate action. Passwords, SMS and other One-Time Passwords (OTP), security questions and even push notifications, contrary to popular belief, are not considered phishing resistant mechanisms as they are all susceptible to some or all of the attacks previously listed. Nonetheless, MFA can be phishing-resistant via a FIDO authenticator for example, and also provide a smooth user experience. According to Forrester, about 80 percent of data breaches are related to compromised privileged credentials.
We can break out the terms Phishing and Multi-Factor Authentication to better understand how they work together to support overall phishing-resistant MFA. Learn more about Phishing.
Phishing definition
- In this case we say phishing, meaning fraudulently inducing victims to reveal personal information, such as credit card numbers and passwords, using some form of social engineering. For example, phishing attackers may send emails that seem to be from a legitimate source, in order to trick victims as described above or perhaps to penetrate the victim’s infrastructure by deploying malicious software such as ransomware, as a precursor to an attack. Spear phishing attacks, vishing, trap phishing, whaling phishing and email phishing scams are all variations of this basic method. Multi-factor authentication phishing is another term sometimes used, and is essentially the same as previously described, however, targeting systems which are protected with non-phishing-resistant MFA.
Phishing email examples
- A classic example of a phishing email is a fake invoice or email from HR that asks for payment details or other sensitive data.
Spear phishing vs phishing
- Spear phishing is a targeted attack towards a specific person, business, organization or group. Spear phishing emails are a much more personalized form of social engineering that makes use of particular details not widely known, creating a false sense of security with the target, so that they may divulge even more information to the attacker(s). In contrast, regular phishing emails take a less specific, broader approach that involves mass emails to bulk lists of contacts.
Phishing attacks often target privileged users who have access to sensitive data and critical systems, and once initial access has been gained, attackers look to further escalate by compromising other users with even greater privileges from within the defensive perimeter. The only authentication technologies that demonstrably stop these types of cyber threats use public key cryptography, such as commonly found within FIDO security keys and smart cards.
Learn more about Multi-factor authentication.
Multi factor-authentication definition
- What is multi-factor authentication? A multi-factor authentication policy is a technique for authentication in which users are only granted access to an application or website after successfully presenting multiple items as evidence — “something you know”, such as a PIN or password, “something you have”, such as a token or card, and in some cases “something you are”, such as biometrics. This type of authentication system requires more than one distinct authentication factor from more than one source—knowledge and possession for example—for successful authentication.
- Types of multi-factor authentication include facial recognition, fingerprint scanning and other biometric verification techniques, email token authentication, hardware token authentication, smartphone prompt or notification, security questions and SMS OTP authentication.
The need for phishing-resistant MFA has become more apparent in recent times. Some experts estimate that as of 2020, spear phishing is linked to upwards of 95 percent of all successful attacks against organizational networks in both the private and public sectors. 2021 also saw some of the largest security breaches ever, including the Colonial Pipeline and SolarWinds hacks. In an attempt to address the growing threat, the White House released its cybersecurity executive order and Zero Trust Strategy with the Office of Management and Budget (OMB), mandating US federal agencies to use only multi-factor authentication (MFA) that can resist phishing attacks by the end of 2024.
What are Phishing-Resistant MFA Components?
There are several components that can be attributed to phishing-resistant MFA. The following should be considered.
Strong binding between authenticator and user identity
- A trust relationship needs to be established to ensure both parties know each other. This can be achieved through a cryptographic registration process that can include an identity proofing process in addition to registering a user’s authenticator for strong binding.
- Regarding the US federal government specifically, an ID proofing process is used to issue an access card to an employee, typically PIV or CAC. Once the relationship has been established, the binding phishing-resistant MFA registration ceremony can then be performed, and once completed, future authentication sessions are assured to be solely between the registered authenticator and the relying party. The most crucial component in the trust relationship is the private key residing on the authenticator, which is to be always protected.
Elimination of shared secrets
- Establishing the trust relationship allows for the authentication mechanism to be based on unique public and private keypairs that perform a secure asymmetric cryptographic ceremony. The authentication ceremony can never be performed without the private key, which to be truly secure, must be stored in hardware that can be attested and not be exportable.
Only respond to trusted parties
- Regarding authentication scenarios susceptible to phishing, attackers will use various methods to fool a target user into sharing sign-in credentials, SMS or OTP codes. Attackers can go as far as creating fake, but familiar looking websites, use social engineering or even bombarding targets with push notification requests hoping to frustrate users enough so that they might disregard common security measures and ultimately accept any authentication requests. Authentication solutions need to resist this verifier impersonation attack in order to qualify as phishing-resistant. In other words, phishing-resistant MFA methods respond only to valid requests from known and trusted parties.
User intent
- User involvement is required to both initiate and authorize a login action, which needs to be clearly understood by the user, and not for example, out of frustration from a flood of SMS or Push notification requests by an attacker. Authentication requests should only exist as part of an access request that the user initiated. Public key cryptography, along with the user action, significantly reduces the attack rate and the entire attack surface.
Given the considerations above, we can see how some MFA solutions either meet or fall short of being truly phishing-resistant. To satisfy the new requirement, two authentication methods have become the industry standard, namely smart cards (PIV) and FIDO2/WebAuthn. The cornerstone of secure authentication systems is asymmetric cryptography, with private key material secured in a hardware device preferable to software alternatives. Solutions that leverage asymmetric cryptography also need to implement all of the points mentioned above. Both of the aforementioned standards qualify as phishing-resistant options.
Types of Phishing-Resistant MFA
Based on public key cryptography, phishing-resistant MFA eliminates the use of shared codes, hence significantly reducing the ability of attackers to intercept access codes and replay them. Phishing-resistant technologies also verify the validity of both the source and destination, resulting in limited authentication action that can only occur between the intended site and the user’s device.
The OMB M-22-09 Zero Trust strategy from the White House specifically describes two phishing-resistant technologies: the FIDO2 WebAuthn standard and PIV smart cards.
PIV smart cards use cryptography based on Public Key Infrastructure (PKI), a cornerstone of secure systems for over 25 years. PKI technology is also widely used for credit cards, e-passports, and physical access control.
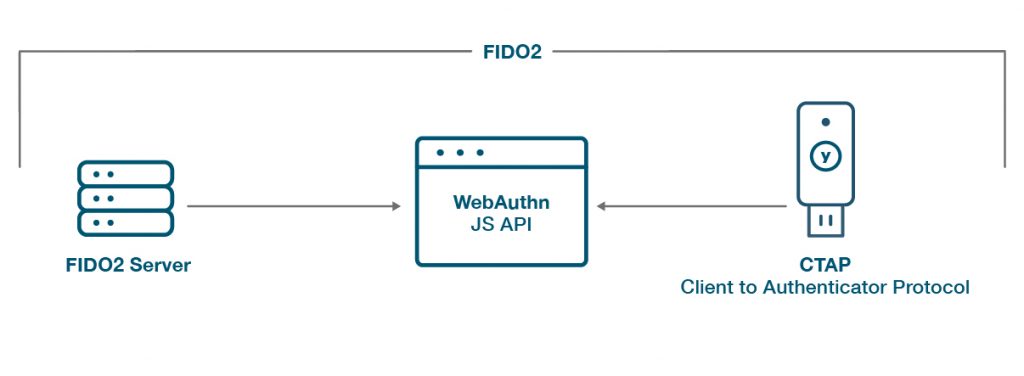
WebAuthn & FIDO delivers next generation phishing protection. Developed to support online authentication without any shared secrets, the protocol was contributed by the FIDO Alliance in 2013 under the name U2F (Universal 2nd Factor), but has seen incremental improvements and has currently evolved into FIDO2, a global authentication standard that even includes passwordless MFA. FIDO2 comprises two industry standards (namely WebAuthn and CTAP2) that work in concert. WebAuthn enables online services to use FIDO Authentication through a standard web API, while CTAP2 is an application layer protocol used for communication between a browser or operating system and an external authenticator.
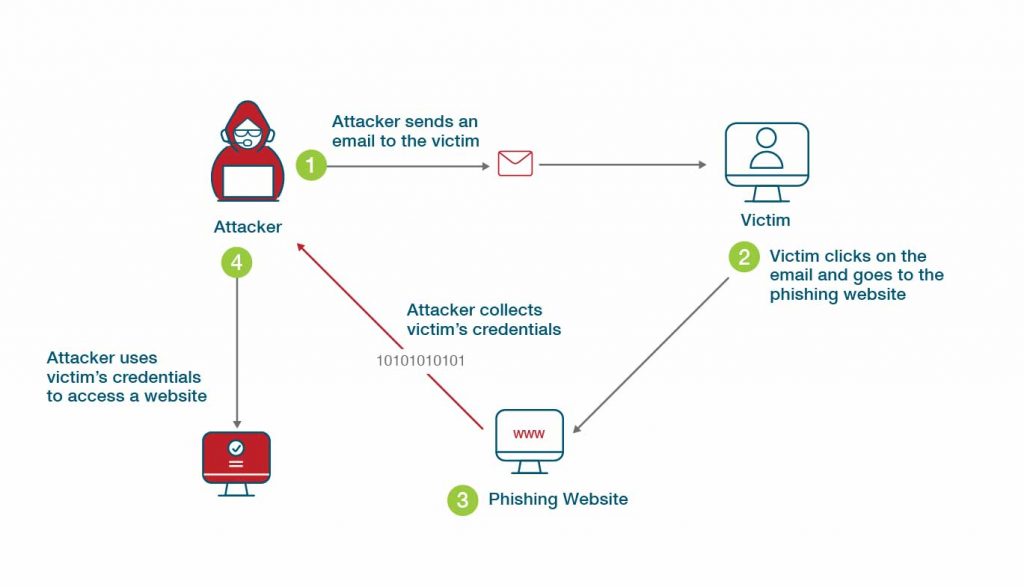
Where Do Phishing Attacks Come From?
Phishing attacks often use social engineering to dupe victims, so they most often come via email, text message or instant message. It is surprisingly easy for attackers to trick most MFA users into clicking on the wrong link sent in a phishing email and therefore revealing a means to gain access to an MFA artifact. The link will likely capture login information such as a password, MFA codes, and anything else the user might unknowingly divulge. The attacker can even take over the victim’s session ultimately, by capturing and replaying the access control information.

As an example, consider the easily hackable Google multi-factor authentication system. The attacker spoofs an SMS message from Google tech support to the victim demanding a backup code, which are commonly used as a fallback to other forms of registered 2FA. The victim then goes to their Google account security page and generates 10 such codes. If the victim responds with one or more of the generated codes, the attacker in turn, is able to provide one of them to login and take over the account. All the attacker needs to know to initiate such an attack is the victim’s phone number and Gmail address, which are generally not that difficult to obtain and sometimes freely distributed by the users themselves.
Of course many SMS recovery systems are much easier to hack than Google’s MFA, and spoofed recoveries are another attack vector. Phishing push-based MFA is also an issue, particularly when end users are not vigilant about approving only logins that they themselves initiated.
Most multi-factor authentication solutions are actually highly susceptible to phishing. No MFA solution should be simply able to be bypassed using a rogue link in a phishing email. FIDO2-compliant MFA devices, for instance, require pre-registration by legitimate websites and devices that ensure MFA solutions only provide authentication codes at the right times and to a verified destination.
Multi-Factor Authentication Examples
You can have MFA with each of these systems below, but you need to be clear on which of these options are phishing-resistant and which are not. The list is by no means exhaustive and only includes a handful of examples, and it should be noted that many vendors are working to improve their phishing-resistant offering due to the increased risk of traditional MFA solutions.
Microsoft products
- Azure multi-factor authentication
- Azure Active Directory including Office 365 multi-factor authentication helps protect access to applications and data, by providing another layer of security by using a second form of authentication. Organizations can enable multi-factor authentication (MFA) with Conditional Access to make the solution fit their specific needs. There are ways to use Azure with the FIDO and PIV protocols for phishing-resistant MFA.
- Microsoft traditional
- Manage multi-factor authentication for Windows log-in with PIV by default, which can be leveraged for all the on-premise connected systems.
Salesforce multi-factor authentication
- As of February 2022, Salesforce multi-factor authentication is required. Security keys, some third-party multi-factor authentication apps, and the Salesforce Authenticator all work for multi-factor authentication in Salesforce.
Google products
- Google Authenticator implements two-step verification using a time-based OTP or HMAC-based OTP algorithm for user authentication, compatible with the Google Authenticator or other third-party OTP apps. There is also the possibility for users to register FIDO security keys with their G-Suite account for phishing-resistant level security.
Facebook/ Twitter
- Most of the popular social networks support FIDO based phishing resistant MFA with FIDO security keys.
Phishing Examples: Recent Phishing Attacks
The 2021 Application Protection Report found that phishing was the second most frequently observed initial attack technique culminating in a successful data breach. An average of 2.3 billion credentials are stolen each year according to the 2021 Credential Stuffing Report, and although email delivers most social engineering attacks, other communication platforms are also experiencing an uptick, according to one-third of IT professionals over the last year, including video conferencing platforms (44%), cloud-based file-sharing platforms (40%), workforce messaging platforms (40%), and SMS (36%).
A study by APWG found that the most common kind of phishing attack, responsible for about 34% of phishing attempts, is targeted towards users of Software-as-a-Service (SaaS) and webmail. Gmail users in particular appear to be heavily targeted.
Phishing-Resistant MFA Protection Benefits
There are many benefits of multi-factor authentication, but nearly all of them presume the ability to resist phishing. MFA increases security with outside organizations but also any other third parties both active and passive. It more precisely controls access to files, internal networks and other system resources, and provides a mechanism for organizations to meet their security and regulatory requirements.
Going beyond just vanilla MFA, and Implemented as phishing-resistant MFA, it also removes the risks of using a password or other shared secrets, and delivers the strongest online security. Phishing-resistant MFA assures consumer identity and ensures compliance with Single Sign-On (SSO) solutions.
Best Practices for How to Stay Protected with Phishing-Resistant MFA
To better understand how to protect yourself or your organization with phishing-resistant MFA, consider the Zero Trust Strategy issued by the Office of Management and Budget (OMB). The document requires federal agencies to use only phishing resistant multi-factor authentication by the end of 2024. This follows President Biden’s recent cybersecurity executive order directing federal agencies and companies engaging with them to move toward modern, phishing-resistant multi-factor authentication (MFA). The EO also requires the OMB to develop an implementation plan for Zero Trust architecture and strategy.
These changes are a formal recognition of the connection between stolen login credentials and the vast majority of cyberattacks, including those based on ransomware. The phishing-resistant technologies the OMB strategy draft specifically mentions are PIV Smart Cards and the FIDO2 WebAuthn standard.
Both forms of phishing-resistant MFA are based on public key cryptography, eliminate shared codes and thus nullifying an attacker’s ability to intercept credentials, and ultimately limit authentication action so it can only take place between the destination and the user’s device. Implementing these standards are the best known and most secure ways to prevent phishing.
Best Practices If You Get Hit By Phishing
A few steps should be taken in the event you detect a potential or are the victim of a phishing scam:
- Ensure any user attributes such as phone numbers have not changed as they can be used to reset account access
- Check for suspicious transactions or account activity
- Speak to employees about the event and anything they may have observed or done, including clicking on any links or opening any attachments
- Conduct a forensic analysis to search relevant system logs for signs of compromise, firewall logs for suspicious network traffic including unrecognized URLs and IP addresses, a record of who sent and received the phishing email as well as its headers and attachments, and the logs of any real-time auditing solution for suspicious activity related to privileged user accounts and sensitive data
- Adjust spam filters and email security settings to ensure similar messages are blocked in the future
- Research for the attack online including what to expect, possible further recovery steps, and potential preventative steps
- Inform all employees to mitigate future attacks and raise general awareness
- Contact the spoofed organization and show them the phishing email so they can inform their customers and be aware of the issue
- Report the phishing attack to the Federal Trade Commission (FTC)
Does Yubico Offer Phishing-Resistant MFA Protection?
Yes! The YubiKey uses FIDO2 and PIV to offer phishing resistance at scale supported by all leading browsers and platforms, and hundreds of IAM and cloud services.
One of the most highly recommended techniques by security experts for fighting phishing attacks, is a hardware security key. This method requires both proof of possession and the presence of the user to login or gain access. Hardware security keys are an ideal option for strong phishing-resistant MFA because they don’t require external power or a network connection, and they don’t publish stored data. They also deliver a great user experience (UX), letting users log in with a single tap or touch on the security key. YubiKeys specifically, have no breakable screens, are both crush-proof and water-resistant, and can be used in sterile environments where smart devices are prohibited.
After years of standards development and security innovation, Yubico is uniquely positioned to help organizations meet current and future security requirements.
As one of the core members of the FIDO Alliance, Yubico partners with Apple, Google, Microsoft and many others to help support the phishing-resistant technologies proposed in the Federal Zero Trust Strategy. Today, users can deploy the FIPS 140-2 validated YubiKey with WebAuthn and/or PIV.
YubiKeys feature modern protocols such as WebAuthn and FIDO2, as well as FIDO U2F, SmartCard (PIV), OTP, OpenPGP, and more. Just one key works with current and emerging applications but can also act as a bridge to legacy applications as enterprises look toward the future. State and local governments are already securing citizen-facing web services, Criminal Justice Information Services (CJIS) systems, critical applications, election ecosystems, and the myriad number of first responders, and both field and remote workers with YubiKeys.
Find out more about Yubico’s Phishing-Resistant MFA protection here.
Get started

Find the right YubiKey
Take the quick Product Finder Quiz to find the right key for you or your business.

