What is Privileged Access Management?
Phishing-resistant multi-factor authentication (MFA) refers to an authentication process that is immune to attackers intercepting or even tricking users into revealing access information. Each party must provide evidence of their identity but also communicate their intention to initiate through deliberate action.
Privileged Access Management definition
Privileged Access Management (PAM) is designed to define and safeguard identities with special access or capabilities beyond regular users. Specifically, a PAM system allows the organization more flexibility and control over these employees, vendors, partners, other users, and even applications, controlling how and when they have access to specific data and accounts.
Like most other infosec solutions, PAM privileged access management is a combination of people, processes, tools, and technology that work in concert to monitor, control, and secure access to an organization’s critical resources, sensitive data, and assets. The primary objective of PAM is to limit access to the most critical data and assets to only those that require it, but also as a means to monitor all users’ actions and increase the protection of those assets and data. In this way, each organization must define the privileged access management boundaries and which accounts qualify as a privileged user to meet its own needs.
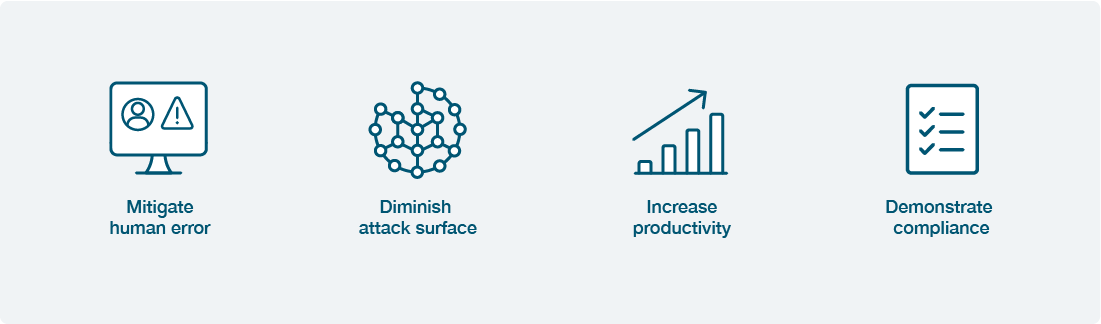
PAM strategies enforce the principle of least privilege, which restricts user account and service account creation and permissions and privileges users based on the absolute minimum demanded by each specific job. The principle of least privilege decreases the vulnerable surface for cyber attackers should an account be compromised, helps prevent the spread of malware, improves productivity, and may even assist in demonstrating compliance.
Privileged access controls offer granular control over sensitive systems to security teams along with the ability to monitor the use of privileged company resources. For enterprise class companies to small businesses, auditing privileged access management systems to ensure they are done correctly can ultimately guard against catastrophic user error and many potential cybersecurity threats.
How does Privileged Access Management work?
According to Gartner, four pillars support the privileged access management lifecycle. These pillars define privileged activities and how privileged access management works for a more secure process that generates optimal value.
Pillar 1: Track and secure all privileged accounts
It is foundationally important to identify privileged accounts because unaccounted privileged access of any duration holds significant risk. This process must be continuous to detect any new emerging risk, since change can happen at unexpected times. Ongoing information collection is essential to providing system administrators and accounts managers with action-oriented data to target and remove inappropriate privileged access and develop governance.
Pillar 2: Govern and control access
Achieve privileged access governance and control via two strategies. First, establish effective privileged access management life cycle processes to verify that all changes to privileged access account credentials are known. Next, implement robust tracking of what every privileged account can access.
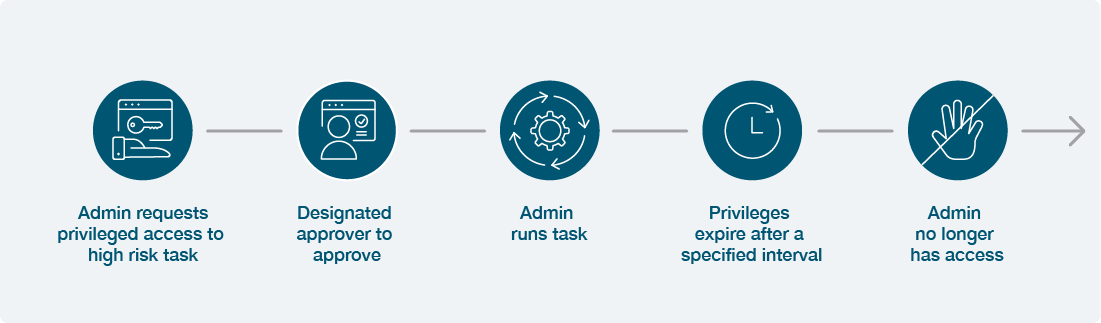
Just-in-time access is recommended for privileged users where applicable, because it grants no standing privileged access, and instead grants access only for short periods and then removes it.
Pillar 3: Record and audit privileged activities
An effective PAM policy demands visibility into changes and the actions of privileged users. Using a combination of privileged access management tools and policies whenever feasible, is often the best way to establish the desired level of visibility.
Privileged access management solutions typically include privileged session recording, which can visualize privileged activity in a way that enables quick and easy retrospective detection of unusual activity in recordings and logs.
Pillar 4: Operationalize privileged tasks
Building up a privileged access management process flow can overshadow automation initiatives. Target repeatable, predictable tasks for automation such as software installations, simple configuration changes, log management, service restarts, startup and shutdown.
Value can be added here with a cohesive mix of privileged access management vendors and tools. For example, administrators can manage the PAM account life cycle with an identity, governance and administration (IGA) tool, provide Just-in-time PAM access with change control management tools, and even enforce access to the PAM tool with single sign-on and multi-factor authentication.
Resting on these structurally sound pillars, a privileged management system reduces operational complexity, improves visibility, and secures the network.
Furthermore, centralizing administrative access reduces frustration and complexity and improves productivity. Granting privileged accounts broad access can result in security breaches and major disruptions. PAM ensures a holistic approach to workflow, so operational complexity does not spiral out of control as administrators follow distinct protocols across operating systems or entire networks. Managing access privileges centrally allows system administrators to maintain more control and users to access needed systems using single sign-on integration without the need for multiple password management.
Monitoring privileged activity enhances visibility across networks, empowering “superusers” to identify issues and respond to them in real time. Admin accounts can observe all activity from beginning to end for each privileged user, enhancing not just security, but simplifying auditing and compliance requirements, helping businesses comply with regulations such as ISO 27001, SOC 2, HIPAA, GDPR, and DSS.
Privileged access management secures remote access, both hybrid versions and cloud-forward configurations. With the rise of fully-remote and distributed workforces, more infrastructure automation tools, software as a service (SaaS) applications, and service accounts accessing the system from multiple locations are now the norm. More granular control and visibility to secure access to cloud and hybrid environments is required than what a Virtual Private Network (VPN) can deliver.
Managing access privileges limits opportunities for user error and malicious attacks, leading to increased security at a very basic level. Privileged access management allows organizations to prevent and respond to both insider threats and external cyber attacks, reducing the attack surface by establishing least-privilege access for processes, users, and applications to reduce potential for attacks and limit damage when they occur.
Why is Privileged Access Management important?
Why do we need privileged access management? Both simple user error and actual malice can present substantial risks to all organizations, particularly through unmanaged accounts, which is why privileged access management is important.
In an effort to save labor and/or reduce friction, system administrators sometimes provide too much access to users. Too much access may mean password sharing for instance, with the same privileged account being accessed by multiple people, or unnecessary privileges for a single user. Either way, such access can cause catastrophic harm, if a user who lacks proper training or knowledge enters the wrong command, modifies an active directory or deletes an important file.
Admins may also allow a single account to operate multiple applications or services in a bid to simplify network access. But on this type of account, a simple mistyped command can impact systems across your network, causing far-reaching damage.
Of course there are risks far beyond simple human error. Bad actors, whether they are hackers who breach systems and find credentials, or former employees who have not had their access revoked, may access privileged information, sensitive data, and powerful systems. Motivated searchers can gain network access using stolen credentials to progressively move and search for the key assets and data they can use to hurt an organization.
Additional security risk arises from privilege creep as employees change roles, and gradually accumulate rights beyond what they require for their current roles, and admins fail to scale back or audit access accordingly. Accidentally or not, such employees may perform unauthorized tasks, again causing serious harm.
A comprehensive privileged access management policy reduces these risks and limits organizational vulnerability.
Privileged Access Management best practices
A strong privileged access management solution demands adherence to several best practices:
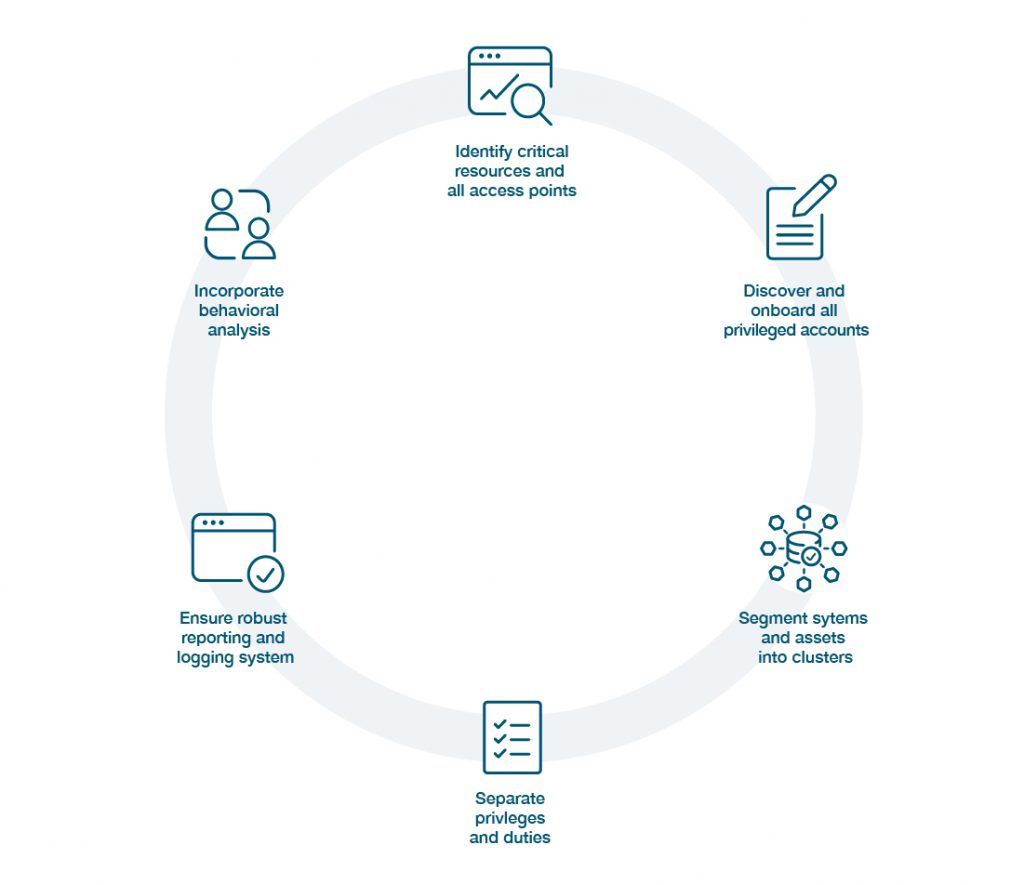
Create a formal privileged account policy. The policy should outline access rights and required privileges for each role it defines within the organization. The team tasked with shaping this policy should consider which privileged account types exist in the organization, who needs access to them, and for how long. Whenever possible, segment operating systems and networks to make it simpler to contain breaches.
Alter or remove default IDs, embedded credentials, and privileged device and service account passwords. Machine accounts often ship with easy-to-guess passwords and excessive privileges. Audit all such systems and update credentials and privileges to match organizational requirements.
Educate the team. Ensure they are aware of security best practices concerning phishing, strong passwords, and password sharing. Rotate credentials routinely, use SSO to keep passwords hidden, and implement multi-factor authentication. A smarter, more skilled team of users is better able to be proactive with cyber security.
Enforce the principle of least privilege. Both machine and human accounts should be restricted so they have the precise permission and account creation levels to access only the resources their defined roles require. Set dates for expiration of privileged access as appropriate. Pay particular attention to the principle of least privilege when employees change roles and during onboarding and termination.
Conduct a detailed inventory. Know which SaaS accounts, cloud applications, and other third-party systems are present. Employees should follow the same robust privileged access management policies with external and internal resources. Ensure no privileged accounts go unmanaged by watching how third-party vendors and contractors access your network closely.
Reduce the attack surface. Rotate, vault, and manage privileged account secrets on premises and in the cloud, including machine learning environments, containerization services, and platforms for infrastructure automation. Reduce the likelihood of attacks—and how much impact they can have—by limiting sensitive credential lifespan.
Monitor, analyze, and audit privileged session activity. Limit how problems can spread by increasing network visibility—and the team’s ability to detect malicious activity and repair catastrophic user errors. Resource owners must follow specific regulatory schedules, and in the absence of those guidelines, perform annual privileged access reviews.
Review privileged access management policies regularly. As your organization restructures, scales, or adopts new technologies, ensure that your best practices are still meeting existing risk-management and security needs.
What are Privileged Access Management requirements?
Privileged access management requirements vary somewhat from organization to organization, but they are the practical implementation of the aforementioned PAM best practices. There is no realistic way to achieve privileged access management requirements and reach the standards set by best practices without using privileged access management tools.
So, what exactly does a PAM tool do? Privileged access management solutions provide a secure, centralized, visible platform to manage the most sensitive access. These privileged management access services and tools vary in many ways, but have several shared, core capabilities:
- Auditing. Provides a clear audit trail by monitoring and recording privileged session activity.
- Automation. Improves policy adherence and eliminates manual intervention by teams such as DevOps, by replacing cumbersome or menial tasks with automated processes.
- Compliance. Aids in compliance with regulations like GDPR, HIPAA, ISO 27001, SOC 2, and DSS.
- Convenience. Creates more transparent workflows
- Credential management. Vaults and rotates credentials such as passwords to shorten how long they are valid.
- Role-based access control (RBAC). Avoids privilege creep and enforces the principle of least privilege by engaging in role-based restriction of network access.
- SSO integration. Conceals passwords, centralizes access to accounts, and improves overall user workflow.
For a recent discussion of various privileged management access solutions, see Gartner’s magic quadrant for privileged access management (PAM).
Identity Access Management vs Privileged Access management
The EU Revised Directive on Payment Services (PSD2) requires strong customer authentication (SCA) of payment service providers within the European Economic Area. Sometimes called strong consumer authentication, SCA is designed to i
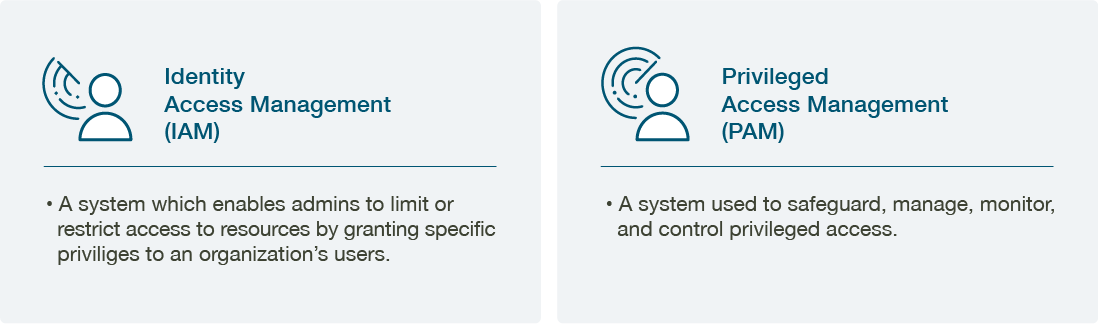
Identity Access Management (IAM) aims to achieve productivity by defining the scope and role of every single user in an organization to ensure they can do their job efficiently and correctly. In contrast, the objective of privileged access management or PAM is to secure data and reduce the risk of exposure or a data breach by monitoring and creating a system of privileged vs. non-privileged accounts to limit access.
However, it is possible and beneficial to use PAM and IAM together. For example, IAM can help define which functions and roles have permission to access critical, sensitive data as the team builds out PAM processes.
Often used interchangeably with privileged access management, privileged identity management (PIM) involves controlling, monitoring, and managing access to crucial resources for privileged users. Finally, privileged session management (PSM) is a feature of superior vendor privileged access management solutions that enables administrators to monitor, control, and record privileged access sessions. PSM can also include auditing and reporting, remote session monitoring, SSH and RDP logging, and workflow coordination.
Benefits of Privileged Access Management
Why implement privileged access management? Implementing privileged identity and access management within your organization is among the best strategies for reducing risk from both internal and third-party sensitive data incidents.
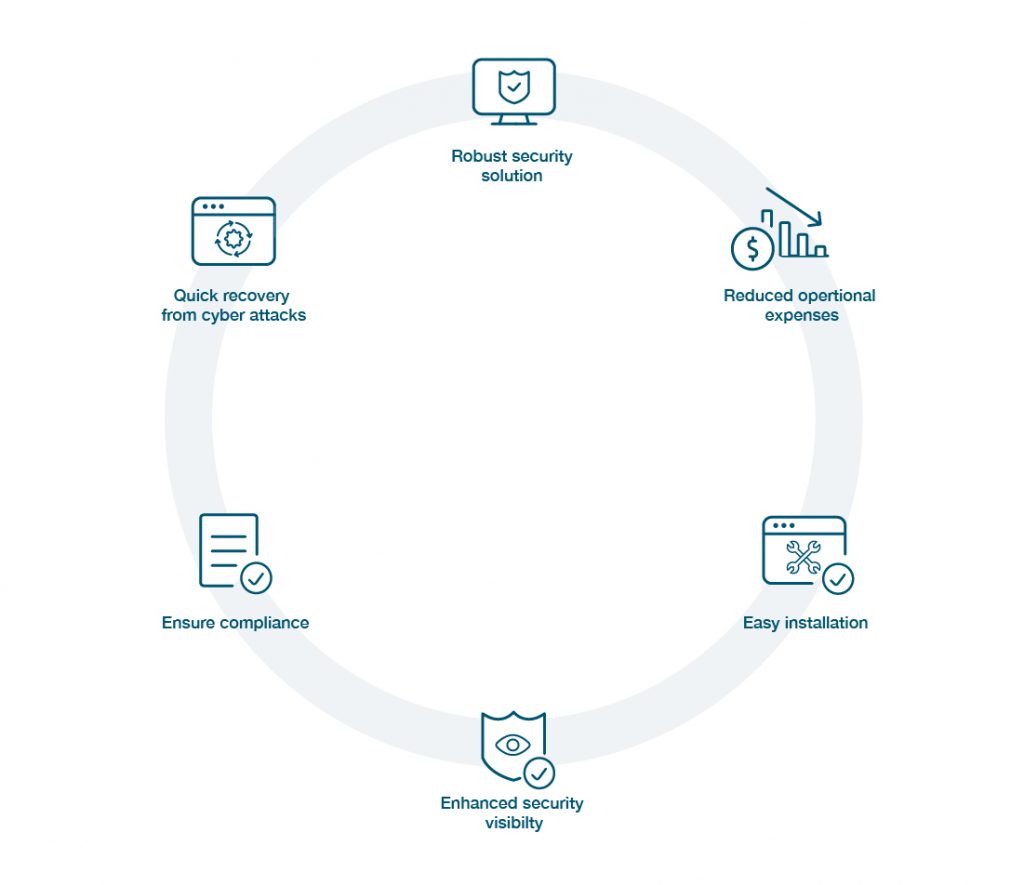
Grant Access to Critical Data Only to Those Who Require It
Privileged access management services drastically reduce points of access to critical assets and sensitive data. Without the right PAM solutions in place, third parties and any employees can access critical resources regardless of need, intent, or training.
Exclude Malicious Parties
All PAM systems require approval before granting access to a particular asset or account. This adds a layer of defense against hackers accessing enterprise data.
Monitor All Suspicious Activity
Privileged access management systems monitor and record which parties access data and assets. Should the organization experience data loss, data exposure, or even breach, the record from the privileged access management software could reveal key details that may prevent future attacks.
Achieve Compliance
Most privileged access management solutions on the market create audit trails, enable two-step authentication or multi-factor authentication, and restrict or limit access. This allows users to comply with specific regulations and present a record of relevant activity when audited.
Render Stolen Credentials Unusable
Privileged access management providers and systems bolster traditional security measures by adding separate controls in addition to the login and password. This may prevent stolen credentials unusable by malicious hackers if administrators act in a timely manner.
Centralize Access
As more applications, vendors, and employees increase an organization’s overall footprint, many security organizations face a visibility and awareness challenge from the broader organizational attack surface. Privileged access management (PAM) software can help restrict critical information access is centralized, leading to more effective monitoring and asset visibility.
Does Yubico offer Privileged Access Management protection?
Yes. Privileged access management is critical, because varied threat vectors put privileged accounts and users at serious risk. The YubiKey protects an organization’s privileged users from account takeovers—prime targets for cybercriminals—by ensuring they meet a higher security bar for authentication in the first place.
Statistically, most security breaches involve misuse of privileged credentials. This can result in devastating consequences for a business, exposing trade secrets, business plans, intellectual property, and financial data.
Additionally, because YubiKeys support a variety of protocols, they can be used to bridge legacy MFA to modern and robust protocols such as FIDO2 and WebAuthn. The YubiKey’s secure element design also prevents private and cryptographic information from being stolen or copied, making it ideal for authenticating privileged users.
YubiKeys are designed to stop phishing, account takeovers, and other user targeted attacks. A YubiKey cannot be fooled even if a user can be tricked into revealing their credentials by social engineering; only designated counterparties can authenticate with the device.
Finally, the YubiKey delivers strong security and a better user experience (UX), which can drive higher user adoption. Always accessible, YubiKey works with a single touch, which can be up to four times faster than typing in an OTP for example. This also lowers IT operational costs and reduces password support incidents by up to 92%, increasing productivity for privileged users and saving the organization money.
Find out more about Yubico and Privileged Access Management here.
Pay as you go for groundbreaking user authentication security.
For less than a coffee per user/month
Get started

Find the right YubiKey
Contact our sales team for a personalized assessment of your company’s needs.

